
From Wikipedia – “The attack surface of a software environment is the sum of the different points (for “attack vectors“) where an unauthorized user (the “attacker”) can try to enter data to or extract data from an environment.[1][2] Keeping the attack surface as small as possible is a basic security measure.[3]“
An attack surface can be an entry point to cause chaos.
Think of an attack surface as an entry point to an application, data storage, network, compute resource, etc. The bigger the attack surface or the larger the number of attack surfaces, the more vulnerable the resource.
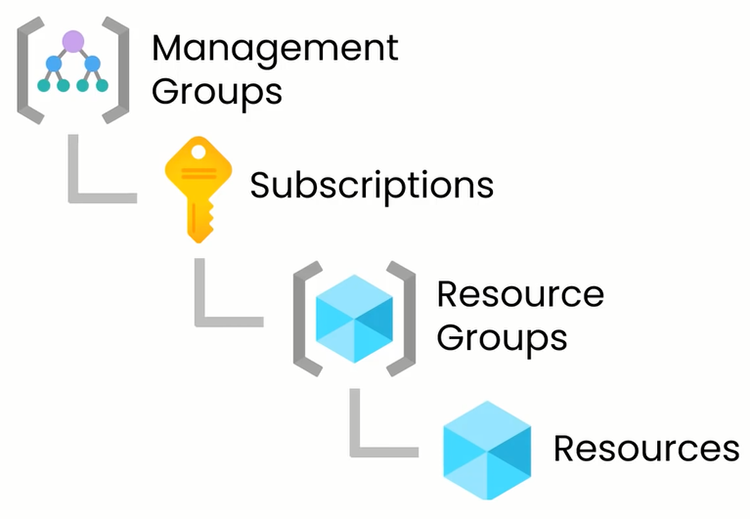
From Bing – “In Azure, a management group is a logical container that allows Azure administrators to manage access, policy, and compliance across multiple Azure subscriptions en masse. Management groups allow you to build an Azure subscription tree that can be used with several other Azure services, including Azure Policy and Azure Role-Based Access Control1.
Management groups support Azure role-based access control (Azure RBAC) for all resource accesses and role definitions. These permissions are inherited by child resources that exist in the hierarchy. Any Azure role can be assigned to a management group that will inherit down the hierarchy to the resources2.
You can use management groups to aggregate policy and initiative assignments via Azure Policy. A management group tree can support up to six levels of depth. This limit doesn’t include the tenant root level or the subscription level. Any principal, whether a user or service principal, within an Azure AD tenant can create new management groups3.”
In Azure, Management Groups, Subscriptions, Resource Groups, and Resources are attack surfaces.
From Microsoft –
“Your resources, resource groups, subscriptions, management groups, and tenant collectively make up your resource hierarchy. Settings at the root management group, such as Azure custom roles or Azure Policy policy assignments, can impact every resource in your resource hierarchy. It’s important to protect the resource hierarchy from changes that could negatively impact all resources.
Management groups now have hierarchy settings that enable the tenant administrator to control these behaviors. This article covers each of the available hierarchy settings and how to set them.”
Detailed steps on how to protect Management Groups, Subscriptions, and Resource Groups in Azure can be found here.
I have been leveraging Azure for over a decade. I have read reams of documentation on how to secure resources in Azure and reduce attack surfaces. I wrote this post to emphasize the importance of securing Management Group, Subscription and Resource Group containers in Azure.
Discover more from Threat Detection
Subscribe to get the latest posts sent to your email.
