
A more detailed explanation can be found in the document SP 800-207.
Identity – The New Perimeter
From NIST — “Zero trust (ZT) provides a collection of concepts and ideas designed to minimize
uncertainty in enforcing accurate, least privilege per-request access decisions in
information systems and services in the face of a network viewed as compromised. Zero
trust architecture (ZTA) is an enterprise’s cybersecurity plan that utilizes zero trust
concepts and encompasses component relationships, workflow planning, and access
policies. Therefore, a zero trust enterprise is the network infrastructure (physical and
virtual) and operational policies that are in place for an enterprise as a product of a zero
trust architecture plan.”
“The Trusted Internet Connections (TIC) and agency perimeter firewalls provide strong internet
gateways. This helps block attackers from the internet, but the TICs and perimeter firewalls are
less useful for detecting and blocking attacks from inside the network and cannot protect subjects
outside of the enterprise perimeter (e.g., remote workers, cloud-based services, edge devices,
etc.).”
Why Zero Trust? – Protecting the perimeter does not stop internal threats – internal threats being both users and applications local to the enterprise/cloud and those users and applications remote to the enterprise/cloud. In hybrid implementations, the enterprise is remote to the cloud and the cloud is remote to the enterprise.
“To lessen uncertainties (as they cannot be eliminated), the focus is on authentication,
authorization, and shrinking implicit trust zones while maintaining availability and minimizing
temporal delays in authentication mechanisms. Access rules are made as granular as possible to
enforce least privileges needed to perform the action in the request.”
Zero Trust Architecture Logical Workflow

The Zero Trust Architecture (ZTA) is more a logical workflow than an Architecture. The idea is that an enterprise or cloud solution is made up of resources. Those resources can be compute, data storage, key vaults, API services, segmented networks, certificate service, etc. A user, application, or device that wants to access a resource, must first make a request to a policy enforcement point. The policy enforcement point makes a request to a policy decision point. The policy decision point checks to see if the request from the policy enforcement point has the required set of privileges to access a resource. If so, the policy enforcement point grants access to the resource. If not, the request is denied.
- The NIST specification is about a logical workflow.
- The NIST specification is not about a physical implementation.
- The NIST specification is about the principle of least privilege — minimize the possible damage from a compromise.
- The NIST specification is about minimizing lateral movement from one resource to another resource in an enterprise or cloud environment.
Zero Trust – Protect Data

The NIST document on Zero Trust Architecture does not provide in-depth guidance on data protection, data classification and data tracking. However, protection, classification, and tracking of data is an important component of an implementation of a Zero Trust Architecture.
There is this document from NIST on data protection. But it does not go far enough – it is a draft.
There is also a document under FIPS 199 that addresses data classification. That document can be found here.
“Security Objectives
The FISMA defines three security objectives for information and information systems:
CONFIDENTIALITY
“Preserving authorized restrictions on information access and disclosure, including means for
protecting personal privacy and proprietary information…” [44 U.S.C., Sec. 3542]
A loss of confidentiality is the unauthorized disclosure of information.
INTEGRITY
“Guarding against improper information modification or destruction, and includes ensuring
information non-repudiation and authenticity…” [44 U.S.C., Sec. 3542]
A loss of integrity is the unauthorized modification or destruction of information.
AVAILABILITY
“Ensuring timely and reliable access to and use of information…” [44 U.S.C., SEC. 3542]
A loss of availability is the disruption of access to or use of information or an information system.””
“Potential Impact on Organizations and Individuals
The potential impact is LOW if—
− The loss of confidentiality, integrity, or availability could be expected to have a limited adverse
effect on organizational operations, organizational assets, or individuals.2
AMPLIFICATION: A limited adverse effect means that, for example, the loss of confidentiality,
integrity, or availability might: (i) cause a degradation in mission capability to an extent and duration
that the organization is able to perform its primary functions, but the effectiveness of the functions is
noticeably reduced; (ii) result in minor damage to organizational assets; (iii) result in minor financial
loss; or (iv) result in minor harm to individuals.
The potential impact is MODERATE if—
− The loss of confidentiality, integrity, or availability could be expected to have a serious adverse
effect on organizational operations, organizational assets, or individuals.
AMPLIFICATION: A serious adverse effect means that, for example, the loss of confidentiality,
integrity, or availability might: (i) cause a significant degradation in mission capability to an extent
and duration that the organization is able to perform its primary functions, but the effectiveness of the
functions is significantly reduced; (ii) result in significant damage to organizational assets; (iii) result
in significant financial loss; or (iv) result in significant harm to individuals that does not involve loss
of life or serious life threatening injuries.
The potential impact is HIGH if—
− The loss of confidentiality, integrity, or availability could be expected to have a severe or
catastrophic adverse effect on organizational operations, organizational assets, or individuals.
AMPLIFICATION: A severe or catastrophic adverse effect means that, for example, the loss of
confidentiality, integrity, or availability might: (i) cause a severe degradation in or loss of mission
capability to an extent and duration that the organization is not able to perform one or more of its
primary functions; (ii) result in major damage to organizational assets; (iii) result in major financial
loss; or (iv) result in severe or catastrophic harm to individuals involving loss of life or serious life
threatening injuries.”
“Security Categorization Applied to Information Types
The security category of an information type can be associated with both user information and system
information3 and can be applicable to information in either electronic or non-electronic form. It can
also be used as input in considering the appropriate security category of an information system (see
description of security categories for information systems below). Establishing an appropriate
security category of an information type essentially requires determining the potential impact for each
security objective associated with the particular information type.
The generalized format for expressing the security category, SC, of an information type is:
SC information type = {(confidentiality, impact), (integrity, impact), (availability, impact)},
where the acceptable values for potential impact are LOW, MODERATE, HIGH, or NOT APPLICABLE”
Document Tracking
Ever watch a movie – heck – watch politicians — and see documents disappear into the vapor?
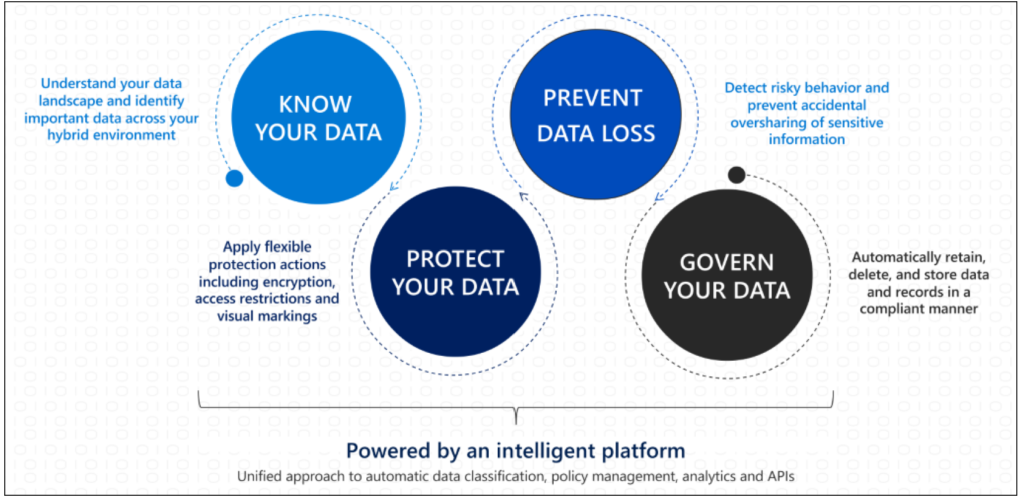
More information can be found here.
If I can get the time, I will post how Azure moves from the abstract to the real world in implementing Zero Trust.
Discover more from Threat Detection
Subscribe to get the latest posts sent to your email.
