
Over sixty years ago, there was a military escalation between the United States and Russia called the “Cuban Missile Crisis”. The two superpowers were locked in a confrontation that took the world up to the edge of nuclear annihilation – Defcon 2.

There were updates from the White House, news broadcasts, etc. President Kennedy had intelligence sources, U2 overflights, conversations in Moscow, etc. which helped in his decision-making processes.

Russia understood the dynamics. The USA understood the dynamics. Both superpowers had access to intelligence sources. Access to these sources was at the nation state level. The average person did not have access to satellite, U-2, RF-101 images, or conversations in the Kremlin. Information was carefully selected by President Kennedy and released to the world, with the purpose of garnering world support for the USA position. Tom Clancy super spook material.
Fast forward six decades to the invasion of the Ukraine by Russia.

In the past, such images would have only been accessible to analysts and defence specialists. The fact that it is now available to the general public at extremely high resolutions signals that average citizens were made aware of potential dangers. Some could even argue that these images prompted evacuations long before official governments took such steps.”
Never before have cell phone users been able to log in to their social media account, watch the near real time staging of a war, the execution of a war, and the impact of the war upon literally millions of folks around the globe.
For some of these folks, they can watch the bullying of a teen-ager and the ultimate suicide of the young person being bullied.
Other folks in a relationship can track the movements of a partner- many times leading to a divorce
I am not convinced this is progress
Open-source intelligence can be thought of as a set of categories:
- Social Media
- Mass media – newspaper, TV, etc.
- Geospatial – Google, Microsoft maps, satellite images
- Meta data and data from pictures and videos.
- Resumes, scientific papers, profiles, etc.
There are two basic groups that use OSINT:
- The viewer
- The researcher that applies sensor fusion to draw conclusions.
I am a collector of information. I merge sensor data and draw conclusions. If I am simply viewing, I am thinking about what I need to do to verify my conclusions.
Collectors of sensor data, most often want to remain anonymous. They want to get in, collect, and get out with minimal chance of anyone knowing they have collected anything. In the olden days, a technical person gained access and collected. Then one or more folks erased the evidence of the collection. Now it is hardware/software.
There are two open-source tools that help the collector maintain anonymity.
One is TOR and the other is Tails.
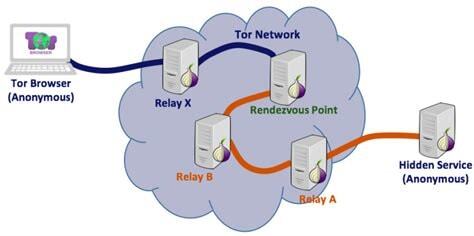
TOR is about getting from point A to point B anonymously. Two points;
- Not everyone is happy when you use Tor – legally happy.
- Tor works,
- Tor is relatively slow because of number of hops.
- That one hop from Relay A to Hidden Service is unencrypted.

Tails is an open-source OS. Free, runs in memory, helps maintain anonymity, Debian based, but there are a few be careful issues.
“Tails is safer than any regular operating system. But Tails, or any software or operating system, cannot protect you from everything—even if they pretend to.”
- If you run Tails on compromised hardware – up to the user to verify hardware is not compromised.
- Protecting your identity when using Tails
- Limitations of the Tor network
- Reducing risks when using untrusted computers
Like life, tradeoffs.
Discover more from Threat Detection
Subscribe to get the latest posts sent to your email.
