Defense At the Perimeter

In days of old, Kings understood, that if they were to remain Kings, that they needed a castle with high walls, a moat, and a draw bridge. The castle had to have space for the serfs to come to trade and feel safe. The start of Defense in Depth. Worked out well for awhile.
The high walls, moat, and a draw bridge worked out well until someone figured out, if they could lob a ball of fire over the high walls, the high walls meant little. The early start to malware.

The consequences were inevitable. The King was no more. The result of thinking: that a defense on the perimeter would win the day.
Attack Timeline and Cost
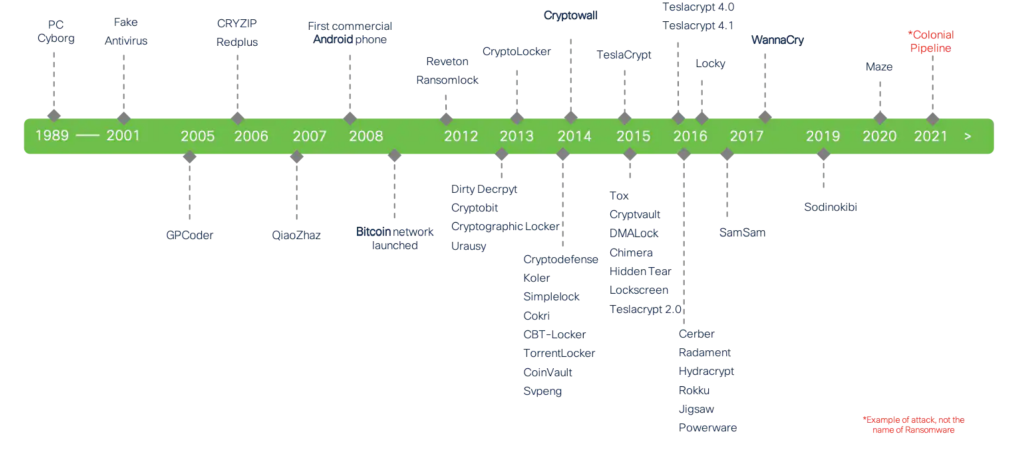
Fast forward a few centuries – fire balls to ransomware. The timeline is from an article posted by Cisco.
The timeline graphic clearly shows more and more successful attacks over a shorter time frame. What is missing?:
- Cybercrime costs the global economy about 1 trillion — 50% more than that predicted in 2018. Also, it is more than 1% of the global GDP.
- The average cost of a data breach in 2020 was a whopping $3.86 million. In 2021 it was $4.24 million.
- A data breach compromising 1-10 million records costs $50 million on average, whereas one compromising 50 million records can cost as much as $392 million. “
Perhaps as interesting as the cost of successful cyber-attacks, is the success of prosecuting cyber-attacks or lack thereof:
Another interesting observation, for centuries the tactic for an attack has not changed. The predator — attacker–formulates a plan. Basic plan, apply pressure, enough pressure, to bring about behavior modification. The goal is to get the prey to open the door so that the predator can successfully attack, pillage resources, and leave. Perhaps the biggest change over centuries is that it is now much easier to get the prey to open the door than it was centuries ago. Hundreds of years ago, the attacker might have to burn down a castle. Today, all the attacker has to do is get the prey to click on a link.
Nist Zero Trust Architecture

NIST has a number of papers on Zero Trust. This image shows an agnostic look at Zero Trust. For me, this picture is too general. It shows Policy implementation and enforcement as being at the center. It does not show any Policy Decision Points. I think of data as being the center of Zero Trust.
The NIST Risk Management Framework (RMF) and Cybersecurity Framework (CSF) from NIST provide guidance – a set of steps – that help get to Zero Trust.
Risk Management
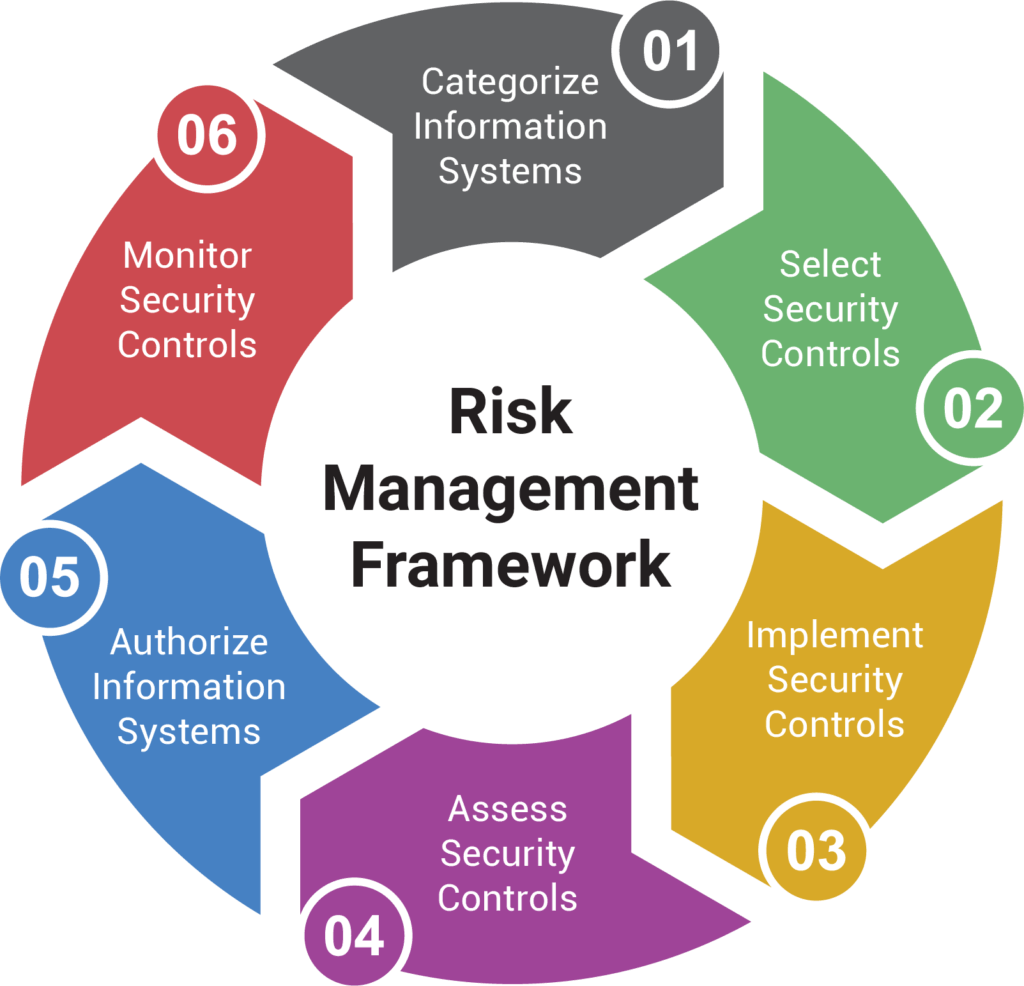
Cybersecurity Framework

Azure Zero Trust

This image, from Microsoft, I think more clearly shows the relationships in a Zero Trust Architecture. The relations are shown by showing flow in Azure Services. In this image, policy enforcement is shown as the center controlling access to Azure Services. Shown are access to Threat Protection, Endpoints, Infrastructure, Networks, Apps, and Data controlled by policy enforcement. In the upper left is the Identity Service. Zero Trust is based upon being able to identify and control granular access to services. On one hand, identifying a user, device, etc. and applying the policies in both a static and dynamic context, is the base of Zero Trust. On the other hand, compromising identities and modifying behavior is why phishing is so successful.
Summary
Zero Trust and Defense in Depth are closely related – control access to everything. I spent a significant amount of time protecting the enterprise. Then I moved onto Defense in Depth. Though Zero Trust applies to both on premise and the cloud resources. it was with Google and GCP that I started learning more about Zero Trust. The controls required to support a Zero Trust Architecture (ZTA) are everywhere. There is well written documentation on how to slowly and very thoughtfully move to ZTA. There are ample numbers showing the cost of compromises – money and reputation. But ZTA’s biggest hurdle, same with security in general, is getting business folks to think of security and ZTA as costs in doing business, not add Ons, but requirements for a successful deployment.
Discover more from Threat Detection
Subscribe to get the latest posts sent to your email.
